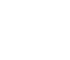RELIABLE END-TO-END IDENTITY SOLUTIONS
Keeping your data secure at all times
TOPPAN Security’s acclaimed line of identity solutions aims at supporting financial institutions, commercial organizations, as well as government authorities to keep their data forgery-proof. We deliver an end-to-end solution for every data securing need to keep individuals all around the world safe and secure.
Our solution:
- do not require user to remember any username or complex password
- highly secure and offer a reliable protection
- featuring state-of-the-art technology
- meeting the compliance standards of major banks.

iDenKey:Mobile Device Binding
Device Binding with iDenKey
iDenKey uses device binding technology to provide second factor for authentication (2FA) in addition to passwords.
With the help of TOPPAN Security’s 3 + 1 layer protection technology, security keys are efficiently obtained and transmitted to the bank terminal. We utilize encryption and asymmetric encryption technologies with dynamic authentication layers in addition to combining multi-factor authentication systems with passwords. As a result, iDenKey achieve optimal security.
These multiple protection measures can prevent data leakages, enhance soft token security, and provide greater security than the traditional username and password format.
Risk based Authentication
Banks offer countless services, all with varying risk levels. However, traditional approaches cannot flexibly respond to these risks, and TOPPAN Security provides a risk-based identity verification solution, which can require users to perform different verification modes according to the risks of service defined by the bank.
TOPPAN Security’s solution provides a flexible system design, eliminating the cost of repeated system modifications. Furthermore, it complies with all the bank policies and requirements while adjusting the identity verification model depending on the calculated risk level.
Evidently, our flexible management systems can adapt to any circumstance and provides users with a smooth authentication and security experience.
iDENFACE:AI-POWERED FACE RECOGNITION
(BIOMETRICS SOLUTION)
AI-powered Face Recognition
TOPPAN Security’s face recognition SDKs and APIs enable comprehensive security and frictionless experiences.
AI-based liveness detection allows for image processing and feature value comparisons with AI models. This technology prevents identity fraud by actively differentiating live images from video recordings, still photos, and even silicone disguises.
TOPPAN Security uses the front camera lens for high-precision face recognition within seconds. Regardless of the mobile device used, the facial recognition process is thoroughly accurate, safe, and efficient. Furthermore, with high system compatibility, the system can be adopted by a wide range of services that require high-standard authentication.
iDENFACE:SELFIE MATCH-ON-CARD (eKYC SOLUTION)

Similarity Check with Selfie photo
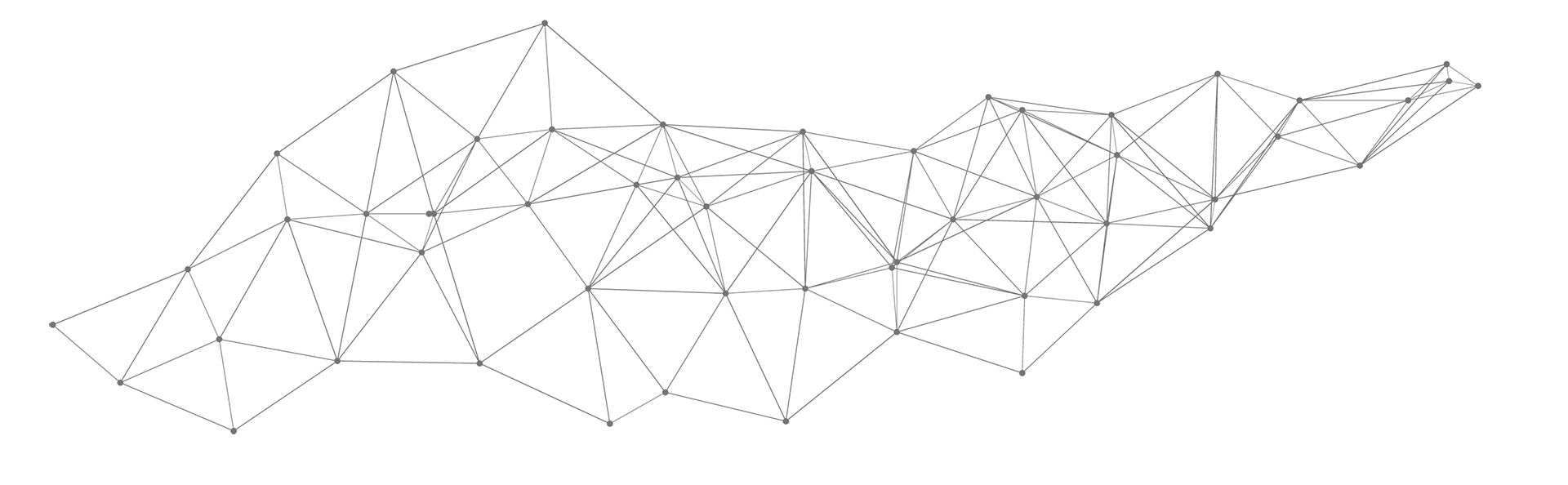
TOPPAN Security technology utilizes user-friendly shooting methods for verification by cross-checking ID card images with selfie photographs.
First, color correction is used to enhance image accuracy and maintain authenticity. Next, the selfie is analyzed with passive liveness detection and AI models for feature value comparisons to ensure that the user and the person on the ID card are indeed the same person. Thereafter, the retrieved data is immediately encrypted to increase the eKYC process’s security.
ID card verification
iDenFace provides facial recognition and similarity cross-checking solutions for authentic identification. This system simultaneously meets regulations and reduces the cost required for manual inspections. Additionally, our solution supports mobile verification on a diverse range of banking services including bank account registration, loan applications, and many other financial procedures.

Advanced technology to keep your data secure
CUTTING-EDGE TECHNOLOGY
Keeping your data secure at all times
Our reliable soft-token security and AI-powered face recognition technologies generate an advanced identity protection for customers and ensure a smooth and seamless user experience.

iDenKey
[cq_vc_accordion accordionstyle=”style2″ contentcolor=”#333333″ contentbg=”#ffffff” titlehovercolor=”#ffffff” titlehoverbg=”#00aced”][cq_vc_accordion_item accordiontitle=”Face ID and Touch ID change detection”]iDenKey applies biometric identification factors, FACE ID and TOUCH ID, as key factors for identity authentication. If there is any change in biometrics or mobile device, it will define as a risk, and the device will be unbound. Once the device is undone, and the user needs to re-bind. TOPPAN Security’s solution uses biometrics factors to ensure that the user is the user himself and keeps track of the mobile device and user status at any time.
[/cq_vc_accordion_item][cq_vc_accordion_item accordiontitle=”End to End Encryption”]
iDenKey uses Advanced Encryption Standard (AES) to encrypt the plaintext message and send it so that every link in the data transmission process always exists in the form of ciphertext. With random key decryption, multiple protections make it difficult for hackers to crack.
[/cq_vc_accordion_item][cq_vc_accordion_item accordiontitle=”Push Authentication”]
When the user makes a transaction, iDenKey encrypts the message and uses a mobile device with a desktop computer/tablet to perform multi-channel transmission and sends the push notification for transaction confirmation. iDenKey design the multi-confirmation method based on the user-friendly and prevent hackers from conducting man-in-the-middle attacks.
[/cq_vc_accordion_item][cq_vc_accordion_item accordiontitle=”Mobile device blocklist”]
There are many types of mobile devices and systems on the market. However, if the system architecture is not rigorous enough, hackers would quickly attack. The strength of the face recognition function of the Android system specification is different. Therefore, TOPPAN Security restricts the Android system mobile phone to only log in by fingerprint.
iDenKey uses a blocklist mechanism as a checkpoint for financial institutions to keep track of mobile phone models that are not fully protected on the market. In addition, to APP security, it also reviews the applicability of mobile devices to provide an additional layer of protection for the overall information security system.
[/cq_vc_accordion_item][/cq_vc_accordion]
iDenFace
[cq_vc_accordion accordionstyle=”style2″ contentcolor=”#333333″ contentbg=”#ffffff” titlehovercolor=”#ffffff” titlehoverbg=”#00aced” extra_class=”toppan-according”][cq_vc_accordion_item accordiontitle=”Liveness Detection”]TOPPAN Security’s solution uses mobile device cameras to capture user selfies. It uses various influencing factors in face images as the feature value selection criteria, such as reflections, reflections, borders, and other information, to prevent paper and video re-shooting from hacker attacks. In addition, our solution can accurately determine whether the face in the picture originated from the user’s shooting, providing a high-intensity biometric verification factor.
[/cq_vc_accordion_item][cq_vc_accordion_item accordiontitle=”A dynamic face recognition system of AI model”]
TOPPAN Security’s face recognition SDKs and APIs enable comprehensive security and frictionless experiences. AI-based liveness detection allows image processing and feature value comparison with AI models, preventing identity fraud by actively differentiating live images from video recordings, still photos, and even silicone disguises.
[/cq_vc_accordion_item][cq_vc_accordion_item accordiontitle=”Secure Source of ID Card image capture”]
When the user takes a photo, TOPPAN Security’s solution will capture the image and encrypt it with Advanced Encryption Standard (AES). Then, transmit the encrypted data to the server for storage, and perform the image feature value analysis and comparison. Data storage and calculation are done on the server, ensuring that the user’s privacy can be protected with the highest security during the verification and analysis process.
[/cq_vc_accordion_item][cq_vc_accordion_item accordiontitle=”Image Resource Detection”]
TOPPAN Security’s solution uses a mobile device front camera for image capture to ensure that all images are captured on the spot by the user instead of non-user operations such as copying, uploading pictures, or color printing. In addition, we do the calibration and error detection to ensure that users provide high-quality images and increase the security in the verification process.
[/cq_vc_accordion_item][cq_vc_accordion_item accordiontitle=”Anti-counterfeiting”]
TOPPAN Security’s ID anti-counterfeiting technology improves the eKYC process. When users take ID photos, TOPPAN Security’s solution will compare key features of the ID, perform detailed color detection, and detect anomalies through the AI model, such as using printed photos and hidden information from images. Ensure that users use the original ID for the registration process and ensure that the ekyc process can be authenticated through mobile devices.
[/cq_vc_accordion_item][/cq_vc_accordion][cq_vc_accordion][/cq_vc_accordion]